While researching the OCPP protocol, which is essential for the electric car charging infrastructure, I discover RFID UIDs of many hundreds of customers on a publicly accessible charging station in southern Germany. I analyze whether these could potentially be misused to charge for other customers. I shed light on security and authentication issues in the charging infrastructure for electric cars.
How does it come to the topic?
I swapped my car for an electric car at the end of last year and have since become familiar with the charging infrastructure in many different EU countries. I was interested to see how the interaction between charging point operators (CPOs), electric mobility providers (eMSPs) and charging hubs works. As a user of public charging stations, you hardly notice any of this.
In principle, the electric charging stations use the OCPP (Open Charge Point Protocol) to communicate with an underlying billing system. This system authenticates the customer and bills the charging process. If the billing system does not know the customer directly, the request is forwarded to other e-mobility service providers via the OCPI (Open Charge Point Interface). One of these partners, who knows the customer, then handles the authentication and billing.
There are various ways in which customers can authenticate themselves at a charging point. These include using an app or an RFID card, either from the charging point operator itself or from an e-mobility service provider. I will discuss a less common method later.
When a customer holds his RFID card up to the charging station, the unique card number, the UID (unique identifier), is read out. The OCPP is then used to start communication with the charging network operator and, if necessary, with other e-mobility service providers via OCPI.
What happened?
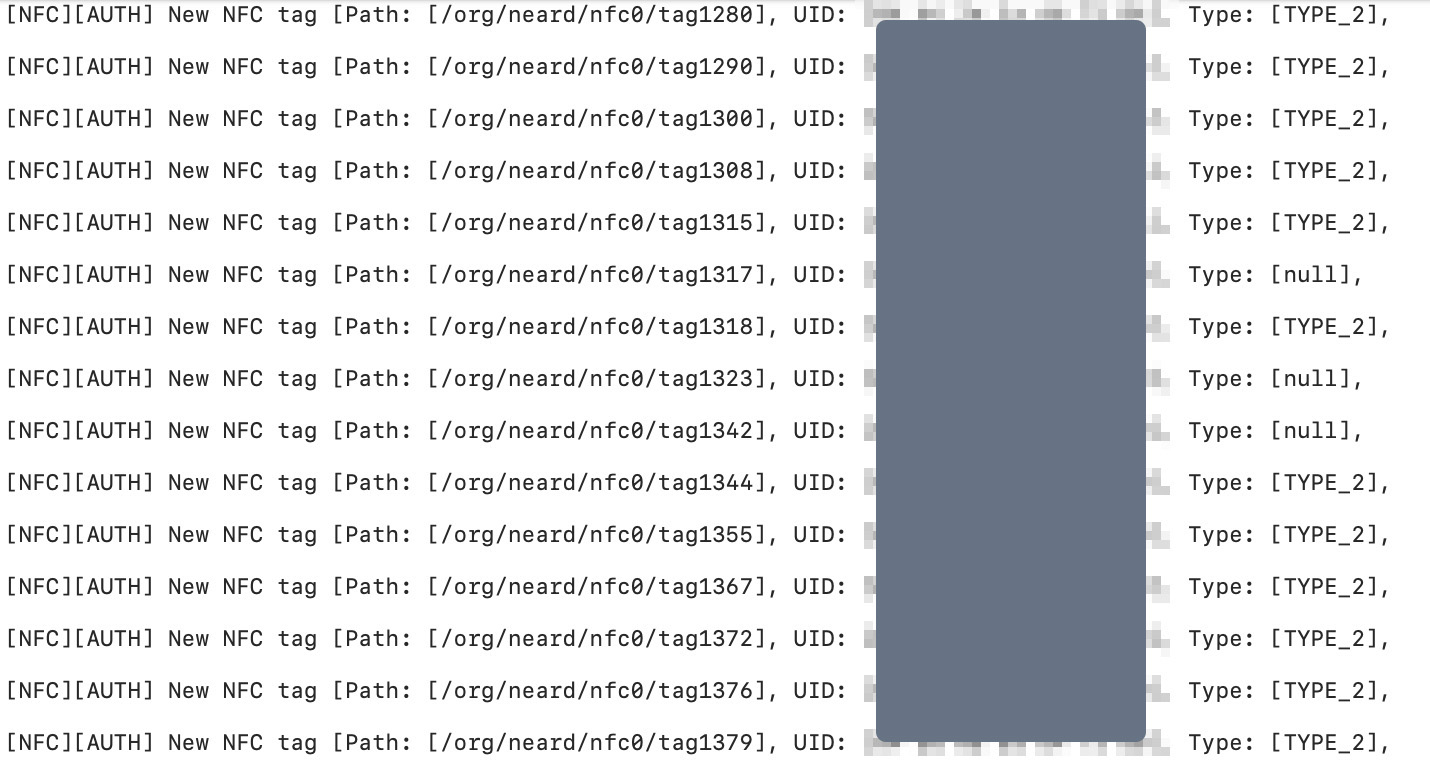
So I came across the unsecured backend of a charging station in southern Germany, which had several hundred customers’ UIDs in its logs from the last few months.
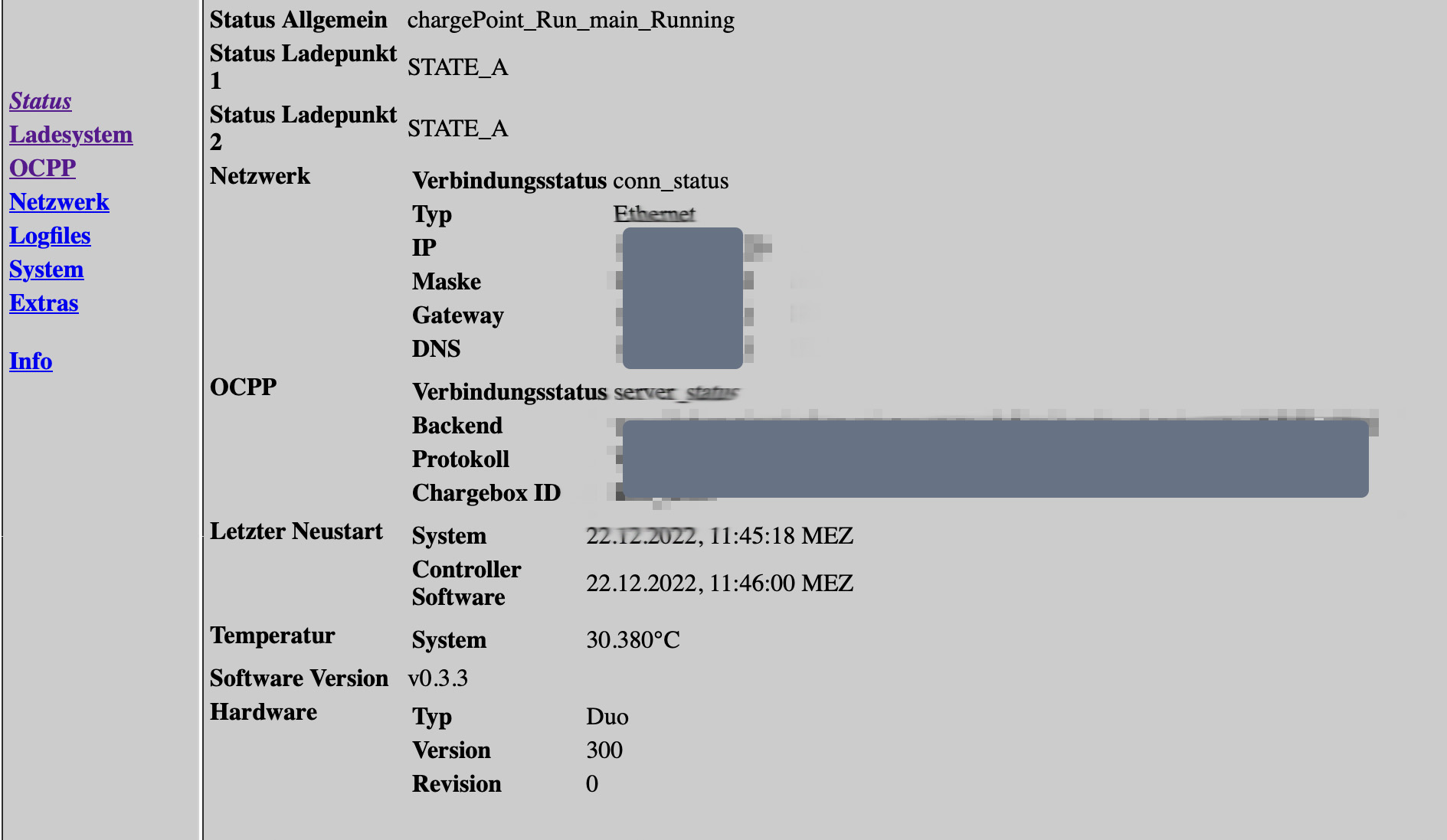
In the web interface of the charging station, the EVSE ID, which is valid throughout Europe, could be found. Thus, the operator ID and the station ID were clear and I could also find the charging station on the map of public charging stations.
Why are UIDs lying around in public a problem?
A few years ago, at a CCC congress, it was discussed that when RFID charging cards are used, only the UID is transmitted as an identifier. I wonder if anything has changed since then? I would like to check if my new eMSP charging card is potentially compromised and someone could charge at my expense if they know my UID, or my UID would be published in the event of just such a data leak.
With a friend, I analyze my charge card to see if it contains any information other than the UID that would allow us to identify the customer. However, we do not discover any such information at first glance. The card is simply a DESFIRE card with a 7byte UID.

We are wondering if our DESFIRE card type on the charging pole reader is an important identifier? However, the FAQ of a major charging station manufacturer lists a variety of compatible card types, so we suspect that the charging station will support all possible roaming cards for compatibility reasons. We program the Flipper Zero with a record of my UID and different card type identifiers (DESFIRE and Mifare Classic).
Although the analysis of my card by the Proxmark3 shows that the card contains even more information than just the UID, we try it only with the super reduced data set of UID and card type on the Flipper Zero.
We visit various charging stations with the Flipper Zero and were able to unlock all of them successfully. Only one ABB charger apparently required the card type identifier of the DESFIRE card. But that’s why we prepared the various data sets beforehand and so we were also able to unlock the column.
What questions need to be addressed?
The use of UIDs as the sole identifier for RFID cards is notoriously insecure. That alone would not have merited a blog article. However, the publication of many UIDs raises new questions:
- How do the parties involved in the charging infrastructure deal with the compromise of card UIDs?
- Are processes initiated to issue new cards to customers or to check whether UIDs have already been misused?
- Do eMSPs ensure that connected CPOs meet minimum security standards?
An open backend connection, although it is annoying, should not be a problem as long as appropriate measures are taken to prevent damage to customers and to learn from the incident.
What happens now?
I contact the charging station operator (CPO) and the associated mobility service provider (EMSP) and point out the problem to them. It is not known to me whether there is a central office that specifically takes care of such data leaks. Whether the UIDs of the cards are personal data according to DSGVO/GDPR, I do not know at this point.
The charging station operator
I contact the CPO by e-mail and share my analysis with him. After thanking me, he assures me that he will contact his IT service provider for the charging infrastructure. Shortly afterwards, I notice that the backend is no longer publicly accessible. When I ask what has now happened to the affected UIDs, however, I receive no answer.
The eMSP
contact, but receive no response for a week. I send my analysis to the info@ email address on their homepage, but again I get no response.
Now an editor from Golem.de takes over the communication and finally brings momentum into the matter. However, I personally never receive an answer from the EMSP even in the further course.
Data protection relevance of RFID cards and their UIDs: Journalist from Golem.de asks important question
It is important to me that the cards are exchanged for the affected customers. The eMSP told Golem.de that the card-issuing EMSP will be informed, but that it is at the discretion of the respective companies to exchange the cards. However, the cards would have been checked for possible fraudulent activities.
A total of 372 cards were affected that have charged at the affected charging station since 07/01/2022.
Whether really cards were / are exchanged I can not track. I hope it but hard for the affected customers.
The Golem.de journalist explores an important question: Are RFID card UIDs personal data under the General Data Protection Regulation and should they have been reported to the relevant state data protection commissioner?
The billing system operator sees the RFID card UIDs only as “technical information” and therefore not relevant to the GDPR, while the data protection authorities of North Rhine-Westphalia, Bavaria and Berlin have a positive view of their relevance in terms of data protection law: the UIDs enable the creation of customer movement profiles and harbor a potential for abuse.
How do we solve the problem that our charging infrastructure is not operated in a timely manner?
Probably not at all.
The emergence of the European charging infrastructure goes back to a time when electricity was still cheap and many CPOs simply gave it away because billing was too expensive. For example, my local municipal utility simply gave me an RFID charging card with unlimited charging volume for a €10 deposit in 2015.
However, the increase in electric vehicles, higher electricity prices and increased utilization of charging stations have led to the disappearance of free charging options. However, the RFID-based authentication method remains. During my research, I found another problem: For publicly funded pillars, charging with RFID cards without reference to a secure authentication method is even part of the funding guidelines.
Contract based charging
Translated from german: The subsidized charging infrastructure must enable contract-based charging. This means that
https://bmdv.bund.de/SharedDocs/DE/Anlage/G/fuenfter-aufruf-antragseinreichung-foerderrichtlinie-ladeinfrastruktur-e-fahrzeuge-anhang-drei.pdf?__blob=publicationFile
charging infrastructure with a charging capacity of 3.7 kilowatts or more, access must at least be provided via RFID card
(Multi Standard, Mifare and comparable standards) and smartphone apps.
Furthermore, additional authentication and billing options (e.g.
ISO/IEC 15118, Power Line Communication) can be offered.
The existing system is in use nationwide and will not be replaced so quickly, as EU-wide compatibility must be maintained. It is important that charging is also possible in other EU countries and that EU foreigners can use our charging infrastructure.
Currently, it is unrealistic for electric car drivers to rely solely on the secure PKI-based authentication system “Plug&Charge”, as only a handful of EMSPs and CPOs support it and the standard must also be implemented in the vehicles via appropriate hardware. The card-based authentication system thus remains the common method, which carries the risk of misuse of the card UID by third parties. Relying on charging apps alone caused me personally significant difficulties during my trip to Norway, as I described here. Thus, card-based charging will remain with us for a good while yet.
Many thanks to Moritz Tremmel from Golem.de for the help. You can find his article on the topic here.
