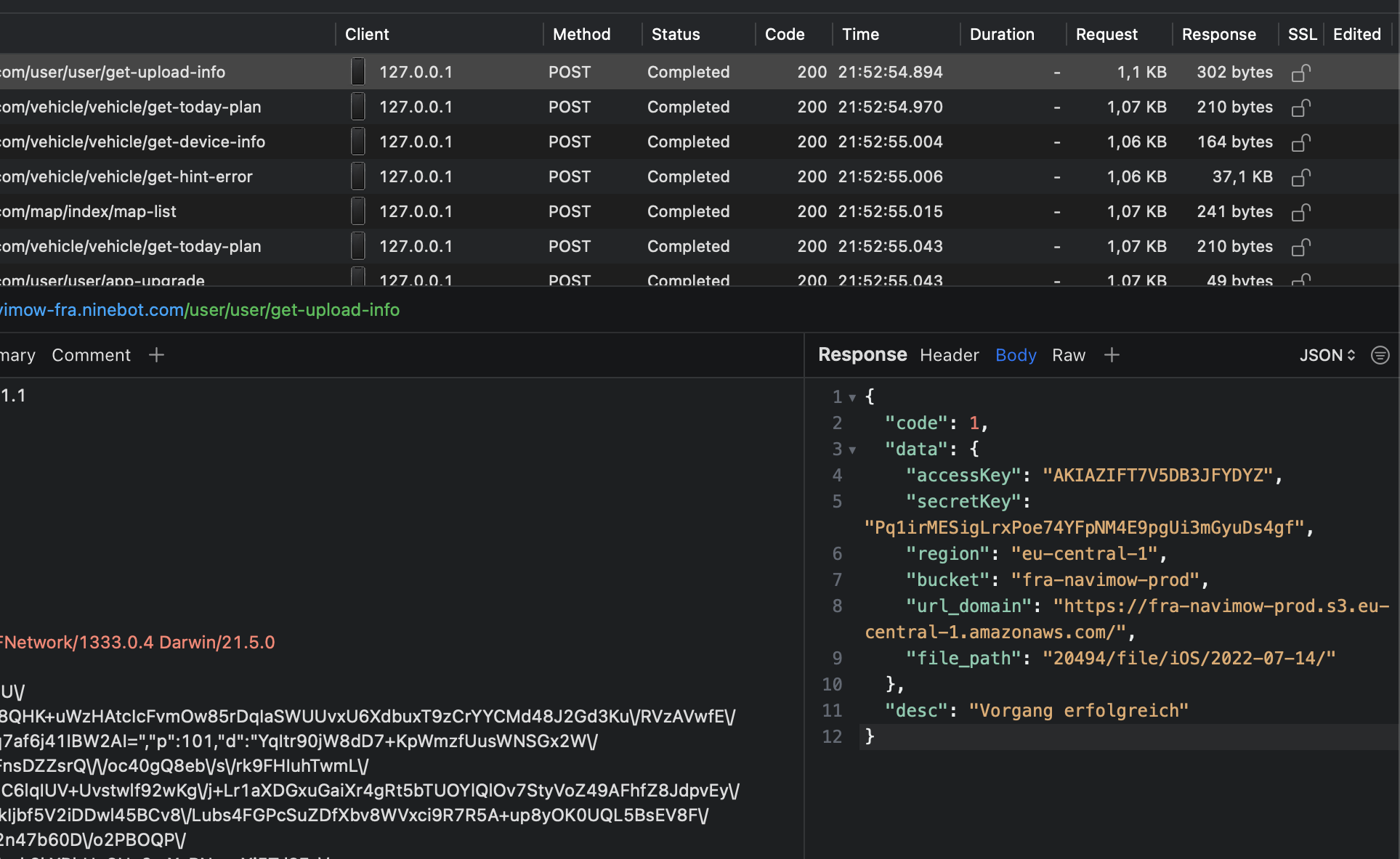
I discovered credentials to the Alibaba Object Storage service in the Ecoflow app traffic that allowed access to corporate data and user data. Poor communication and no adequate response in recognition of the security issue frustrate me
2 CommentsCategory: IT
There are some days in summer when the temperature in the house is a bit too high for my taste.…
1 CommentHowever, devices that only talk to their proprietary app have nothing to do with “smart home”. This is also the…
2 CommentsI find publicly available RFID charging card UIDs and ask myself what the potential for abuse is. I clone my own charging card and, together with a journalist from Golem, ask fundamental questions about the security of European charging infrastructure and probably create a precedent for how to deal with a data leak in such a case.
Leave a CommentIn a thread in the TFF forum I read to the fact that there are charging stations at IONITY, which…
Leave a CommentI’ve already mentioned in previous articles (here and here) that I think the Segway Navimow was launched way too early…
1 CommentIn order to get the most out of our PV system, I would have to change the phases when charging electric cars. Not easy…
Leave a CommentWe do not yet know how we want to use our property in the future. Therefore, it is of course…
4 CommentsI reverse engineer the API of my heating thermostat and can now integrate it with my Home Assistant.
2 CommentsMy PC is shrinking down to a 19L case. Will that work out well?
Leave a CommentThe Microchip POE-USB-PD60 is supposed to be a power supply and USB network card for my Macbook Pro. Unfortunately, it does not work as expected.
Leave a CommentI’ m looking for a silent switch with POE support and fiber optic uplink to power a large portion of my home network. Is the Mikrotik Netpower 16P the perfect device?
1 CommentFor the WLAN installation of 300 access points the construction of adapters for the wall mount was necessary.
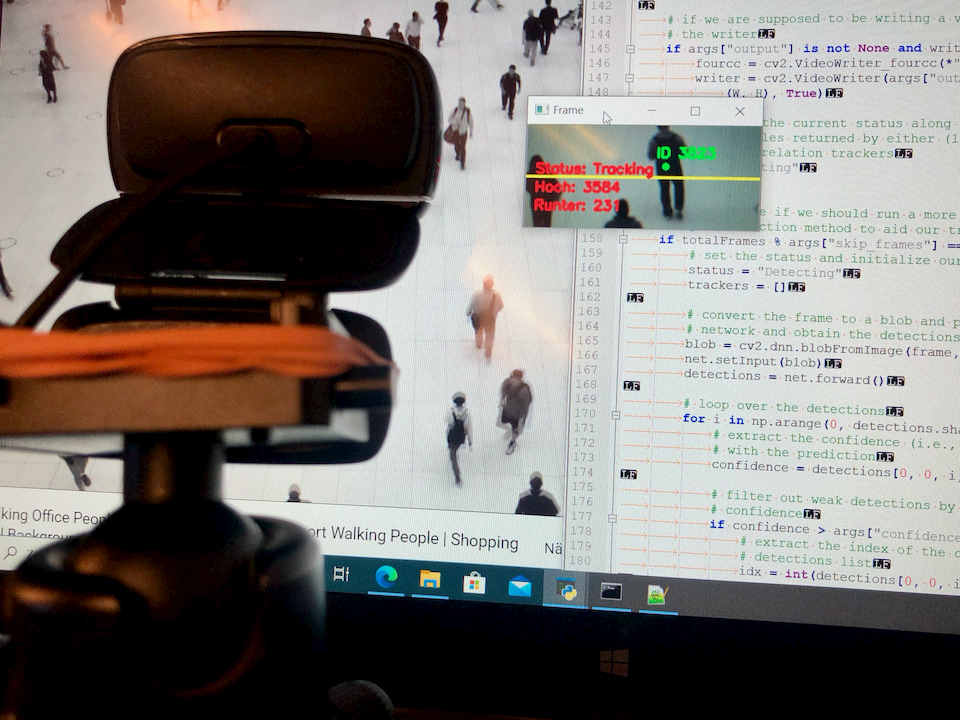
5 CommentsHow well does people counting work with OpenCV? My first steps, problems and first successes.
2 CommentsMore and more white spots on my Philips TV. How to fix them (better than I did)
10 CommentsOne of my AirPods Pros makes annoying clicking noises with the slightest movement. Time for an exchange.
Leave a CommentAll of a sudden all third party apps crash on my iPhone. The fix is easy, if you can find it.
1 CommentA careless moment and fluid is in my MacBook keyboard. How do I clean up the stuck keys?
4 CommentsI had massive problems from the beginning to get the two controllers of the HTC Vive connected to the rest…
Leave a Comment