I’ve already mentioned in previous articles (here and here) that I think the Segway Navimow was launched way too early – but I still wanted to be able to control rudimentary functions from the Home Assistant: Start, stop, read the battery charge, and also extract the map where the device was already mowing.
Segway currently only offers the ability to control the robotic mower from their in-house “Navimow App”, so I recorded the traffic via Proyxman on the iPhone to get an idea of their communication.
I wanted to recreate the control functions in Node-Red, as I did with my Fenix TFT Wifi thermostats. Unfortunately, I failed because although Segway exchanges JWT tokens with the app after authentication, they are presumably only reused in encrypted form in further communication in the app, and so I couldn’t easily recreate the communication without reverse engineering the app – I was pretty frustrated.
A few days later I was on the train with friends on the way to the Netherlands and had a free minute to deal with the project again. I was explaining the cryptic communication problem to my friends on the train when one of them got puzzled by one of the responses:
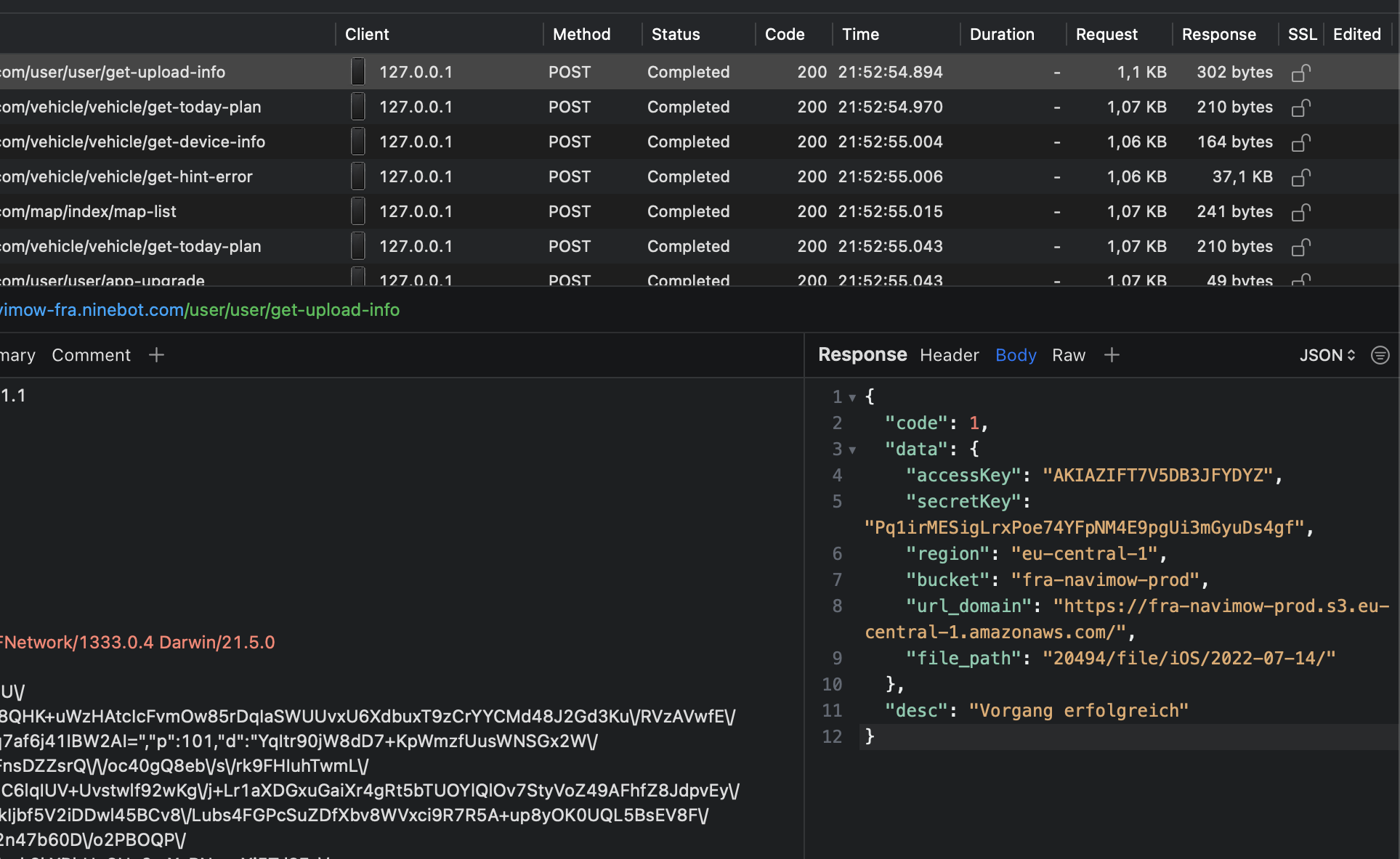
“Wait, what’s that?”
It quickly became clear that these were credentials for an AWS S3 bucket. Still quite interested in what we would find, we logged into the S3 bucket with the credentials from the response and ended up in a logging directory where the smartphone app actually stores its logs. Through HTTP communication, I was already aware of what UserID I had, so I also quickly found my logs from the last few weeks. While browsing, I found GPS coordinates, timestamps, and quite detailed info on how the robotic mower was running.
Wait… we can also see logs of the other users… and open them….
Not good. I’m sure that’s not how it’s supposed to be.
We can see by the number of folders how many European customers have the Segway Navimow, and by experience from our own logs, we also know that for every other customer, we can see their GPS coordinates as well.
The train stops and we have to change trains.
In the back of my mind I still have the uneasy feeling that this way everyone knows exactly where in Europe the devices are located in the gardens.
We arrive in the Netherlands and my friends and i go our separate ways for a few days. In a cafe I sit down again and log back into the S3 bucket. This time, however, I accidentally enter only the access data, but not the target bucket and suddenly see a different folder structure than I expected.
Holy shit…
Actually I finally want to have my vacation….
I realize that Segway not only builds scooters and recently lawn mowers, but also many other devices, some of which I had never heard of before.
Now I feel a bit queasy and call my friend again to clarify what we should do now. Log files are one thing, but this is something else.
In any case, contact Segway’s security team immediately and have the bucket closed. I’m sure Segway doesn’t want something like this openly displayed on the Internet.
Easier said than done. There is no security contact address and even after longer research I don’t know who to contact.
But because I already had many tickets open because of problems with my robot at Segway, I opened another ticket, this time with the urgent request to give me immediately a contact to the security team.
The first level support was not helpful at all at first and asked me to direct the issues to them, which I declined. I wanted to write directly to a developer or security staff member and not get another “we’ll take care of it” message.
Because I didn’t want to give them any information, but they didn’t want to give me the contact addresses, they asked for “proof”, whereupon I put a .txt file with my ticket number on the Frankfurt S3 bucket (yes, writing permissions were also possible) and sent them a link to it:
Dear Support Team,
i think this is proof enough, please see the ticket number:
https://fra-navimow-prod.s3-eu-central-1.amazonaws.com/proof.txt
Please give me the contact of your security team now.
I wasn’t quite sure how the support team would proceed now, but a day later I had a mail from Ninebot in my inbox, in which a member of the security team introduced himself and asked for information about the problem.
From here on things went very relaxed and I was happy to finally write to someone who could solve the problem.
I briefly summarized the problem, how I got the credentials, and that they seemed to work read/write in other parts of Segway/Ninebot.
The bucket was closed a day later and my new proxyman records no longer contained AWS credentials either.
This fixed the issue, but would have been off the table much faster if Segway/Ninebot had put appropriate contact information online right away. Not a chance if I hadn’t already been in contact with Segway support about other issues anyway.
As a little goodie, I got an ultrasonic sensor in the mailbox from Segway a few weeks later as an add-on for my Navimow. Thanks for that and thanks for the friendly communication of the security team.
The review of the Navimow ultrasonic sensor can be found here
[…] my case with Segway, where I discovered a similar security problem, the communication was so much better and more […]